Evidence The Pirate Bay Move To North Korea Was A Prank, In Understandable Terms
Falkvinge on Infopolicy 2013-03-15

Infrastructure: Yesterday’s big story was definitely about The Pirate Bay having moved to North Korea. If you asked the Internet’s infrastructure, the net itself would tell you about the move, and The Pirate Bay issued a press release confirming the story. But reports surfaced that it could have been an elaborate hoax, and closer inspection proves that.
The problem with verifying the story or its debunking was the technical level of expertise required to understand the reports. When you started talking about “traceroutes” and “whois lookups”, you would lose 99.9% of the audience, who would be incapable of independently verifying what you said. When you added in the reports claiming to debunk the story, but which were instead about “Border Gateway Protocol” (BGP) and “Autonomous Systems” (AS) numbers, you lost another 99.9% – including me.
I can’t verify or disprove the report based on BGP and AS numbers. But there’s something else I can use. The laws of physics.
I’m going to focus on the traceroute quoted below. You can think of it in terms of a telephone line trace. It is a list of the way the signals go from your computer to The Pirate Bay. To illustrate, the first hop in the chain from my workstation is my firewall (named firewall.internal.falkvinge.net), and my ISP alltele is visible as a next step in hop #4. The crucial evidence here is in the timings: my firewall is 379 microseconds away from me, and my ISP is 3.3 milliseconds away from me.
You, too, can run this trace from where you are. Open a prompt (in Windows, it’s Windows+R, then cmd and Enter, on a Mac, you run Terminal, and on any flavor of GNU/Linux, you hit Ctrl-Alt-T) and run traceroute thepiratebay.se – on some systems, the command is just tracert thepiratebay.se. It should produce a document similar to the one below.
rick@battlestation:~$ traceroute thepiratebay.setraceroute to thepiratebay.se (194.71.107.15), 30 hops max, 60 byte packets 1 firewall.internal.falkvinge.net (192.168.80.1) 0.379 ms 2 * * * (unknown hop) 3 * * * (unknown hop) 4 h88-129-128-10.static.se.alltele.net (88.129.128.10) 3.327 ms 5 te0-7-0-7.ccr21.sto01.atlas.cogentco.com (149.6.168.49) 3.992 ms 6 te0-3-0-4.ccr22.sto03.atlas.cogentco.com (154.54.60.21) 19.605 ms 7 te0-3-0-2.ccr22.ham01.atlas.cogentco.com (154.54.73.65) 22.574 ms 8 te0-3-0-6.ccr22.fra03.atlas.cogentco.com (130.117.49.213) 28.316 ms 9 francetelecom.fra03.atlas.cogentco.com (130.117.14.178) 35.297 ms 10 xe-3-2.r00.dsdfge02.de.bb.gin.ntt.net (129.250.5.61) 31.762 ms11 213.198.77.122 (213.198.77.122) 31.516 ms 12 * * * (unknown hop)13 xe-0-1-0-3.r02.frnkge03.de.bb.gin.ntt.net (129.250.5.62) 38.855 ms14 xe-0.level3.frnkge03.de.bb.gin.ntt.net (129.250.8.202) 38.566 ms15 vlan90.csw4.Frankfurt1.Level3.net (4.69.154.254) 118.681 ms16 ae-82-82.ebr2.Frankfurt1.Level3.net (4.69.140.25) 122.293 ms 17 ae-61-61.csw1.NewYork1.Level3.net (4.69.134.66) 130.630 ms 18 ae-21-70.car1.NewYork1.Level3.net (4.69.155.67) 132.708 ms 19 INTELSAT-IN.car1.NewYork1.Level3.net (64.156.82.14) 135.094 ms20 209.159.170.215 (209.159.170.215) 202.517 ms21 202.72.96.6 (202.72.96.6) 703.997 ms22 175.45.177.217 (175.45.177.217) 707.161 msSo we see 22 hops in the trace, where the last one was famously in North Korea, almost a full second from where we are sitting, 700 milliseconds out. But let’s not look at that for a moment, let’s look instead at hops #16 to #17. Hop #16 is in Frankfurt and hop #17 is in New York or Kansas City. Let’s assume New York; that’s where the transatlantic cables land. Yet, in the trace, they are eight milliseconds apart.
Let’s focus on this. The distance from Frankfurt to New York (measured in Internet signalling time) is reported to be just over twice the distance from my firewall to my ISP. This sets us thinking. What is the physical distance from Frankfurt to New York?
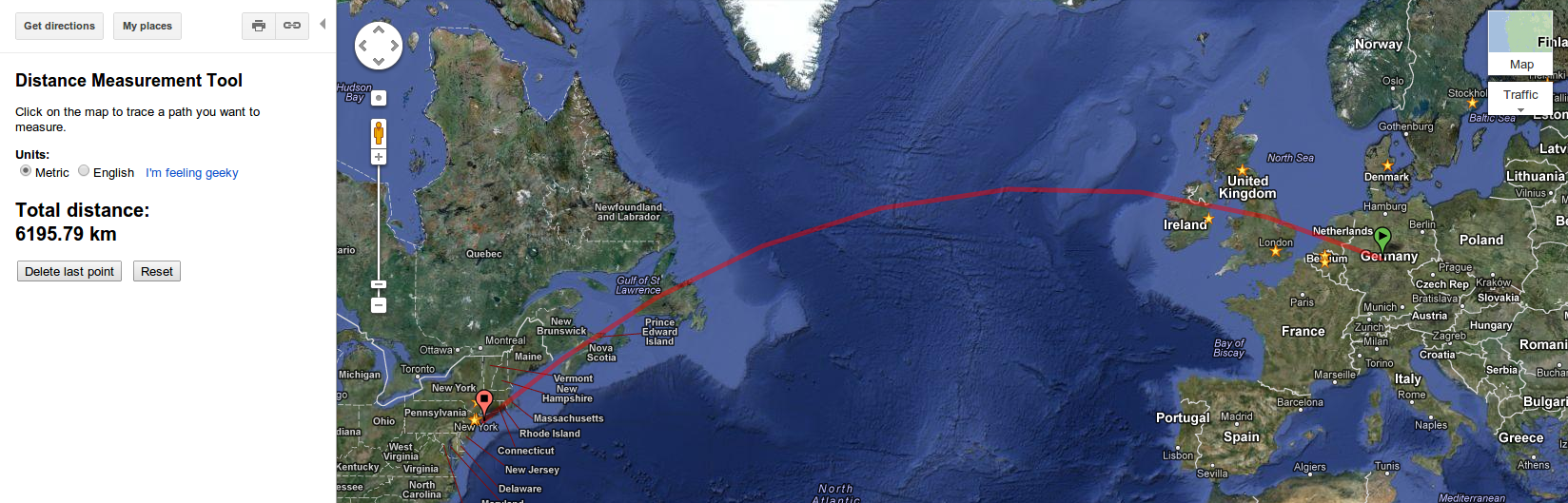
The distance from Frankfurt to New York is 6,195 kilometers.
The physical distance that hop #17 has to cover is 6,195 kilometers. It covers this hop in eight milliseconds. Here, let’s take a look at the laws of physics. What is the speed of light? What is the limit, as told by the laws of physics, to how fast the signals in a fiberoptic cable can cover this distance?
The speed of light is exactly 299,792,458 meters per second. To cover 6,195,000 meters, light needs 0.020 seconds, or 20 milliseconds. But we just saw that the traceroute reported eight milliseconds for this jump. That’s troubling. More precisely, this violates the laws of physics. The traceroute claims that internet signals travel at more than twice the speed of light.
This hop in the traceroute violates the laws of physics. And with that one hop in the traceroute proven to be impossible, the whole traceroute is shown to be an elaborate hoax.
Just to double-check, I am getting ping times of 30-ish milliseconds to the Frankfurt address from Stockholm, Sweden, and ping times of 110 milliseconds to the New York address. Differences of 80-ish milliseconds seem much more reasonable than the eight milliseconds claimed in the traceroute.
So how do you fake a traceroute to this degree? You meddle with the deepest routing logic of the Internet, that’s how. That kind of wizardry goes beyond my horizon. But after observing that the traceroute violates the laws of physics, I can tell with certainty that it is faked.
As Anna Troberg, leader of the Swedish Pirate Party, wrote yesterday; “The joke’s on you. The Pirate Bay is enormously skilled at two things: keeping their site online and lulzing the establishment.”
So with this evidence in hand, where in the world is The Pirate Bay? San Diego? Austria? Cambodia? Still in Oslo? Nobody knows at the moment. Hacking the internet to this degree is deep wizardry far beyond my ability to untangle it.
UPDATE: Some have pointed at the fact that Level3 is a U.S. provider, and that they could name their U.S. routers “Frankfurt”, and that the transatlantic hop actually happened between hops #14 and #15, a hop of 80 milliseconds. This is plausible on first thought. Then again, a geographic lookup places hop #16 in Frankfurt, and I have a ping to hop #16 of 30ms, and to hop #17 of 110, as stated in the article. As usual, there’s no authoritative source for anything and we have to add all the data together to see what we believe or not. Personally, I don’t think the trace hits Level3 at all, I think that entire part is faked. Above all, I don’t think anymore that The Pirate Bay is in North Korea.
UPDATE 2: One way to tell a fake traceroute is to trace it from multiple locations around the globe. In this case, another telltale sign is a traceroute from within Level3, which is a big internet service provider. You will notice the trace starts in Dallas at Level3, moves to Amsterdam, from there to Dresden and Frankfurt, then back to Level3 and then the rest of the route. Anything starting out at Level3, jumping to a different continent, and then going back to Level3 is faked with near-damn-certainty. So everything after Frankfurt is faked; the route above never hits Level3 at all. Is Frankfurt fake too? Well, who knows. But Level3 almost certainly is.