Microsoft: Iran is refining its cyber operations
newsletter via Feeds on Inoreader 2024-02-08
Summary:
Iranian cyber operations targeting Israel, its allies and other Iranian adversaries around the world are becoming more focused, refined and increasingly bold, researchers with Microsoft said late Tuesday.
Iranian-linked cyber operations spread across a mix of government entities and contractors are also showing more signs of collaborating with each other, a development that Microsoft researchers caution may make Iranian operations targeting American critical infrastructure and the 2024 elections more difficult to foil.
Published by the Microsoft Threat Analysis Center, the analysis breaks Iranian-linked cyber and influence operations linked to the Israel-Hamas war into three distinct phases: at first, reactive and misleading, then all hands on deck, and more recently expanding in geographic scope.
In the immediate wake of the Oct. 7 Hamas attack on Israel, Iranian-linked cyber operations were reactive and opportunistic. In several instances, Iran-linked groups claimed to have carried out damaging new attacks that were either fabrications or recycled operations from as much as a year earlier.
That dynamic gave way to an increase in the number of groups involved in targeting Israel — 15 Iranian-linked groups tracked by Microsoft, up from nine — alongside a shift to destructive and sometimes coordinated attacks.
By November, the Iranian-linked groups widened their scope to carry out attacks against countries and entities believed to be aiding Israel and hit targets likely to undermine international political, military or economic support for Israeli operations in Gaza, the researchers said.
This broader set of targets included the United States, Bahrain, Albania and the United Arab Emirates. This dynamic made national news when a group calling itself the “Cyber Av3ngers” targeted programmable logic controllers manufactured by an Israeli company in November, including one located in a water utility in Pennsylvania.
The U.S. government publicly linked that operation to the Islamic Revolutionary Guard Corps Cyber-Electronic Command (IRGC-CEC) and sanctioned six Iranian officials for their role in the attack last week.
“The IRGC’s attacks on US water control systems while opportunistic were seemingly a clever ploy to test Washington by claiming legitimacy in attacking equipment made in Israel,” the researchers said.
This kind of operation is an example of Iranian-linked operations targeting countries and private companies perceived as aiding Israel while hiding behind a flurry of personas and false-fronts online linked to both the IRGC and Iran’s Ministry of Intelligence and Security (MOIS).
Hacking personas and front groups in Iran are managed and operated through a variety of contractors in Iran, which carry out both intelligence collection and destructive attacks, according to a recent detailed analysis from Recorded Future’s Insikt Group. Such contractors were involved in the sprawling Iranian operation targeting the U.S. elections in 2020 that included purported emails from the Proud Boys sent to Democratic voters and attempts to infiltrate multiple news websites to modify and create content to undermine election reporting.
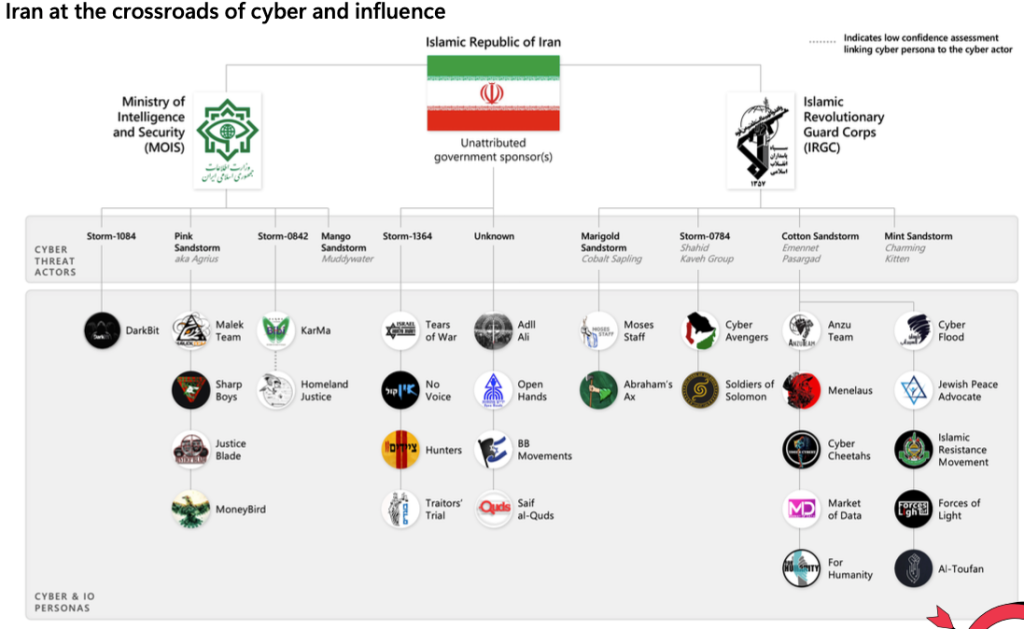 A breakdown of some of the Iranian-linked cyber personas tracked by Microsoft Threat Intelligence, including possible affiliations (Microsoft Threat Intelligence).
A breakdown of some of the Iranian-linked cyber personas tracked by Microsoft Threat Intelligence, including possible affiliations (Microsoft Threat Intelligence).
Another operation, carried out by a suspected IRGC persona known as “For Humanity,” used artificial intelligence as a key component of an influence operation.
That operation saw Iranian hackers disrupt several news channels with a fake news broadcast in the UAE, Canada and the UK. “We no choice (sic) to but to hack to deliver this message to you,” the hackers wrote in a message that was displayed on the breached channels. Immediately after, an AI-generated news anchor appeared on screen and said: “For the sake of humanity, I want to tell you about some of Israel’s crimes against the Palestinian people.”
The use of an AI-generated talking head marks “new techniques we’ve not seen from Iranian actors,” Microsoft’s researchers said.