So Just Exactly What Is NSA’s Prism, More Than Reprehensibly Evil?
Falkvinge on Infopolicy 2013-06-08

Privacy: The US NSA’s PRISM program appears to be a set of specialized deep-packet inspection filters combined with pre-existing wiretapping points at high-level Internet carriers in the United States. Since the program’s revelation the day before yesterday, speculations have ranged far and wide about who does what to make this surveillance state nightmare possible. Adding it all together, it would appear that the social tech companies did not, repeat not, supply bulk data about their users at the US Government’s will – but that the situation for you as an end user remains just as if they had.
The day before yesterday, news broke – no, detonated – that the NSA named nine social communications companies as “providers” for spy data. Among them were Microsoft, Hotmail, Skype, Apple, and Facebook – no surprises there, activists in repressive countries say “Use once, die once” about Skype – but also companies like Google and Gmail. This raised a lot of eyebrows, not to say fury.
The idea that the companies you trust with your most private data were handing that data wholesale to today’s Stasi equivalents was mind-bogglingly evil and cynical. As the news of this broke, the companies would have been a lot better off if they had just been found out doing something like eating live children.
The impression that companies were playing an active part in providing private data to the NSA was strengthened by the precision of the presentation – that there were dates when each company had, as it seemed, voluntarily joined the surveillance program.
Seeing the companies in question scramble to deny the allegations of the NSA deck – first from on-duty spokespeople with their polished façade, then from CEOs – was the inevitable next step. But this is where things became interesting. While the initial polished façade was barely credible, the response from the CEOs came across as surprised, open, and candid.
So far, there are three parties to this story: the NSA with its leaked slide deck naming the nine companies as data providers, the media who reported on it, and the companies denying any active part in NSA spy activities. The first reaction is that at least one of them must be lying. But I don’t think any of them are. I think the leaked deck from the NSA is genuine, I think the Washington Post and Guardian didn’t conspire to make shit like this up, and I have come to believe the response from the companies. How could this be possible?
At this point, there are three possibilities of what PRISM is:
1: Social communication service companies are handing the NSA private data automatically, wholesale and/or on request. This was the initial impression from the deck and the Guardian / Washington Post articles, combined with NSA’s use of “provider” when naming the nine companies.
However, one interesting initial reaction from the companies in question said something quite relevant: “if this is happening, it is without our knowledge or consent”. That leads us to option 2.
2: The NSA is wiretapping a number of key junction points on the Internet in real-time, and have specialized real-time filters to extract information when people use services from the named nine social services companies. We already know about the fiber split box at AT&T, we know about Echelon, we know about at least one court order to Verizon. The fact that the Internet is wiretapped in real time by spy agencies is well-known. How that data is used and analyzed, not so much.
There is also a third option, which is the normal court route of getting a court order to give out a user’s private data, which the New York Times speculated was the Prism program:
3: When presented with a judicial order, companies abide with the law and present as much information as they are legally required, but not more. This has been the case for quite some time, and far predates social communications – and digital communications, for that matter.
Out of these, it would appear that options 2 and 3 are true, but of those, only option 2 is Prism. Option 1 is not true. Here’s why.
When the CEO of Google and their chief legal officer publish a joint blog post named “What the Fuck?”, there’s an element of very candid surprise there. When they word their rebuttal to the allegations in a way that leaves absolutely no loopholes whatsoever,
Press reports that suggest that Google is providing open-ended access to our users’ data are false, period.
…then that comes across as candid fact. So just to empty all possibilities, could they be unwittingly lying – would it be possible for a low-ranking network administrator to have received a secret letter and order to comply with wholesale wiretapping? Would it be possible for the CEO to not know about this? In a word, no. No. That would not be conceivably possible with the traffic volume and patterns required.
Second, this slide from the now-infamous 41-slide NSA deck demands some extra attention:
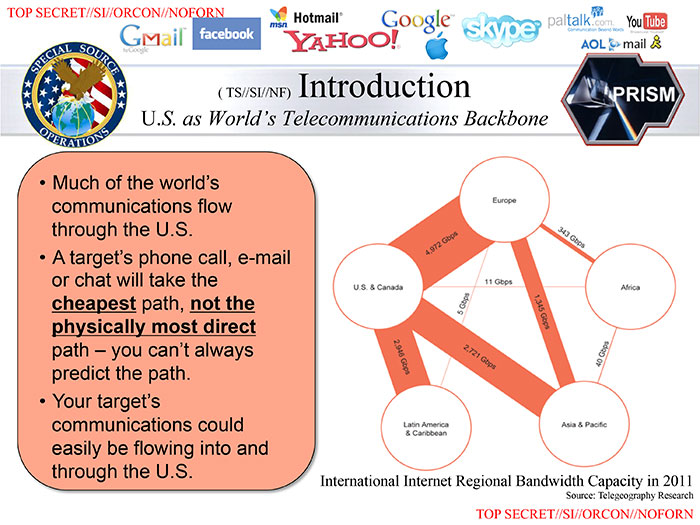
Slide showing how most of the global Internet traffic flows through the United States, with bandwidth between different continents specified.
The 41-slide leaked presentation is allegedly used to introduce the PRISM program to people at the NSA. If companies were willfully handing over private data wholesale as per option 1 above, this slide – worldwide Internet routing paths and bandwidth – would be completely irrelevant noise to the presentation. However, if option 2 was true, this particular slide would be absolutely key to understanding how and why the program worked. You would not be able to make good use of the data analysis without understanding the limitations of how the data is being collected, and this slide answers that question perfectly, albeit at a high level.
This leads us to the following conclusions:
- The FISA court orders requiring disclosure of specific information for specific users are not PRISM. They exist, but are completely irrelevant to this discussion.
- The nine companies named as “providers” have not played the active part that the word implies, or any active part at all.
So in conclusion,
PRISM appears to be an analysis method of the catchall Internet wiretapping we already knew about, an analysis method that specifically targets traffic to and from nine social communications services.
This is obviously still just speculation from the currently available data, but it’s the way all the pieces of the puzzle so far appear to fit together.
The earlier conclusions that privacy is your own responsibility, and the dangers of using a centralized service, well, those conclusions completely remain. But the early notion that the centralized services were complicit in governmental spying appears to have fallen. Active part or not, though, the important part here is that you’re still being wiretapped. You’re still being wiretapped when using these services, regardless of who does the actual wiretapping and who assists and who doesn’t.
To some extent, encryption could probably mitigate the situation. Do you know how to encrypt all your traffic and data? Do you do it? If your answer is no, your social life is getting on file with today’s Stasi, which – by the way – was a German abbreviation for Ministerium für Staatssicherheit, translating literally to National Security Agency.