Microsoft Office Russian Dolls, (Fri, Nov 14th)
SANS Internet Storm Center, InfoCON: green 2025-11-14
You probably know what are the Russian or Matryoshka dolls. It's a set of wooden dolls of decreasing size placed one inside another[1]. I found an interesting Microsoft Office document that behaves like this. There was a big decrease in malicious Office documents due to the new Microsoft rules to prevent automatic VBA macros execution. But they remain used, especially RTF documents that exploits the good %%cve:2017-11882%%.
The document (SHA256:8437cf40bdd8b005b239c163e774ec7178195f0b80c75e8d27a773831479f68f) that I found uses another technique to prevent the RTF document to be spread directly to the victim. The RTF document is placed into the OOXML document:
remnux@remnux:~/malwarezoo/20251113$ zipdump.py mexico_november_po.docxIndex Filename Encrypted Timestamp1 _rels/ 0 2025-10-22 21:55:102 docProps/ 0 2025-10-22 21:55:103 word/ 0 2025-11-12 02:58:504 [Content_Types].xml 0 2025-10-22 21:55:225 docProps/app.xml 0 1980-01-01 00:00:006 docProps/core.xml 0 1980-01-01 00:00:007 word/_rels/ 0 2025-10-22 21:55:108 word/theme/ 0 2025-10-22 21:55:109 word/document.xml 0 2025-11-12 02:59:0410 word/endnotes.xml 0 1980-01-01 00:00:0011 word/Engaging.rtf 0 2025-11-12 02:58:3412 word/fontTable.xml 0 1980-01-01 00:00:0013 word/footer1.xml 0 1980-01-01 00:00:0014 word/footnotes.xml 0 1980-01-01 00:00:0015 word/numbering.xml 0 1980-01-01 00:00:0016 word/settings.xml 0 1980-01-01 00:00:0017 word/styles.xml 0 1980-01-01 00:00:0018 word/webSettings.xml 0 1980-01-01 00:00:0019 word/theme/theme1.xml 0 1980-01-01 00:00:0020 word/_rels/document.xml.rels 0 2025-11-12 02:58:5821 word/_rels/settings.xml.rels 0 1980-01-01 00:00:0022 _rels/.rels 0 1980-01-01 00:00:00The file is referenced in the Word document:
remnux@remnux:~/malwarezoo/20251113$ zipdump.py mexico_november_po.docx -s 20 -d | grep Engaging.rtf<Relationships xmlns="http://schemas.openxmlformats.org/package/2006/relationships">...<Relationship Type="http://schemas.openxmlformats.org/officeDocument/2006/relationships/aFChunk" Target="/word/Engaging.rtf" Id="YAjq8U"/></Relationships>remnux@remnux:~/malwarezoo/20251113$ zipdump.py mexico_november_po.docx -s 9 -d | grep YAjq8U<w:document xmlns:wpc=“http://schemas.microsoft.com/office/word/2010/wordprocessingCanvas” ...<w:body><w:altChunk r:id=“YAjq8U”/>...</w:document>
The RTF document contains a shellcode that triggers the Equation Editor exploit. The next payload is C:\Users\user01\AppData\Local\Temp\license.ini. It's a DLL (SHA256:d8ed658cc3d0314088cf8135399dbba9511e7f117d5ec93e6acc757b43e58dbc) that is invoked with the following function: IEX
CmD.exe /C rundll32 %tmp%\license.ini,IEX A\x12\x0cC
You can see the special characters used as parameters to the function here:
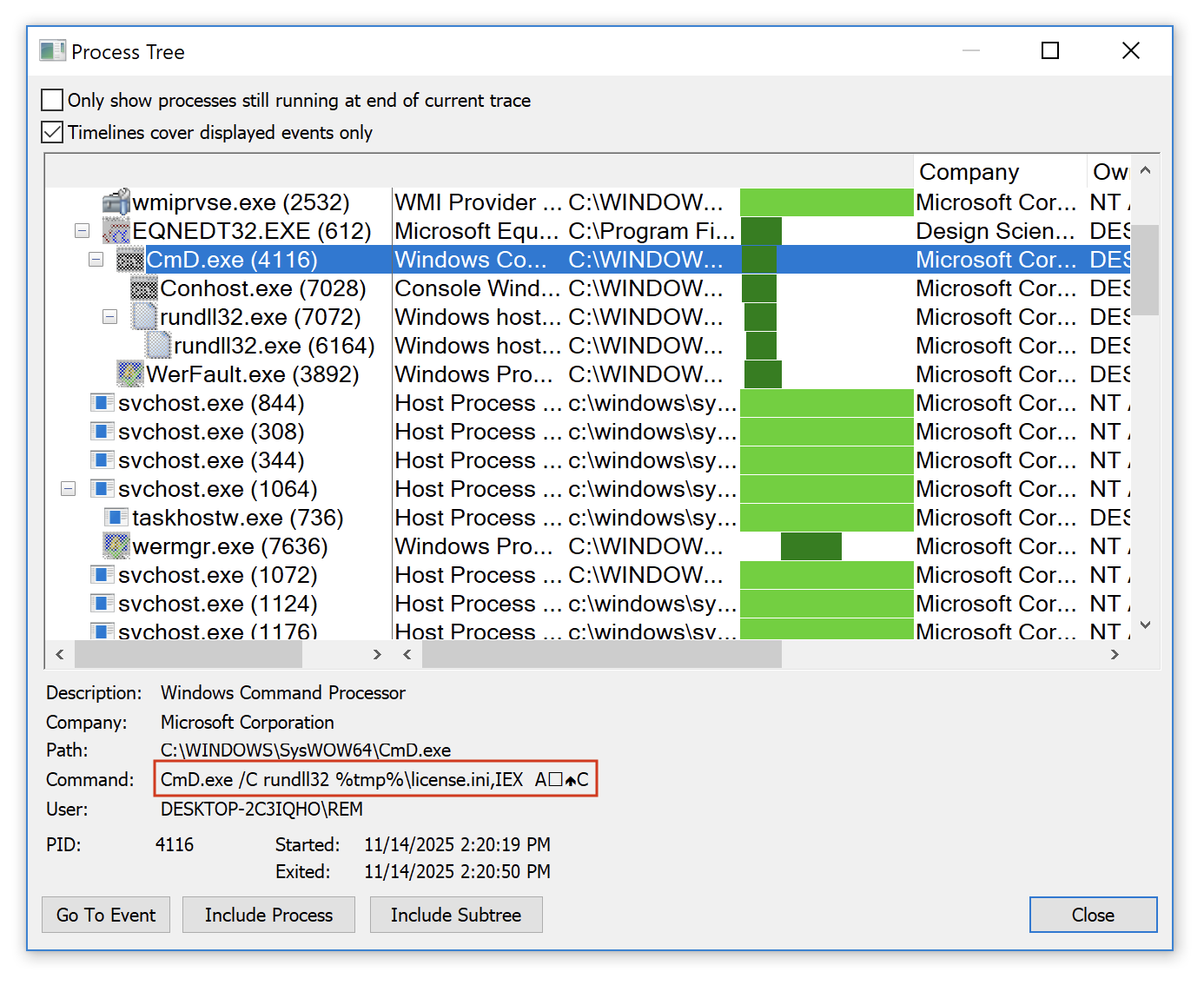
This DLL is pretty well obfuscated, I'l still having a look at it but the malware family is not sure... Maybe another Formbook.
[1] https://en.wikipedia.org/wiki/Matryoshka_doll
Xavier Mertens (@xme) Xameco Senior ISC Handler - Freelance Cyber Security Consultant PGP Key
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.