What sites is Trickbot targeting?
CyberCrime & Doing Time 2020-11-19
Its been a while since we decoded Trickbot configs to see what banks and organizations were being actively targeted. While recently most of the news about Trickbot has been how it drops the Ryuk Ransomware, and that is certainly important, we can't forget that Trickbot is first and foremost a Banking Trojan / Infostealer that is designed to steal website credentials from infected users. While there are many fascinating add-on modules that perform other actions, such as inventorying the network on which an infected machine resides, attempting to dump Windows Domain credentials, and launching remote control backdoors, THE DEFAULT BEHAVIOR IS TO STEAL WEBSITE CREDENTIALS. Every website where the user types data has the data captured and sent to the Trickbot operators, but certain websites are specified for more nuanced interactions, which could be to only steal data from particular sub-pages, or could be to alter the appearance of the website to request additional data not being asked for by the website. This latter behavior is called a "Web Inject" and on Trickbot, they are listed in an encrypted file named "dinj" for "Dynamic Injections." Like many malware researchers, I use the fantastic tools developed by @hasherezade to help decode the configuration files of Trickbot to see what the current collection of URLs in the DINJ file is targeting. 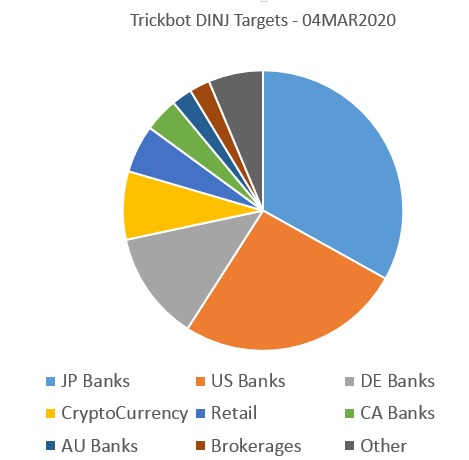 DINJ file breakdown (04MAR2020 by @GarWarner)
DINJ file breakdown (04MAR2020 by @GarWarner)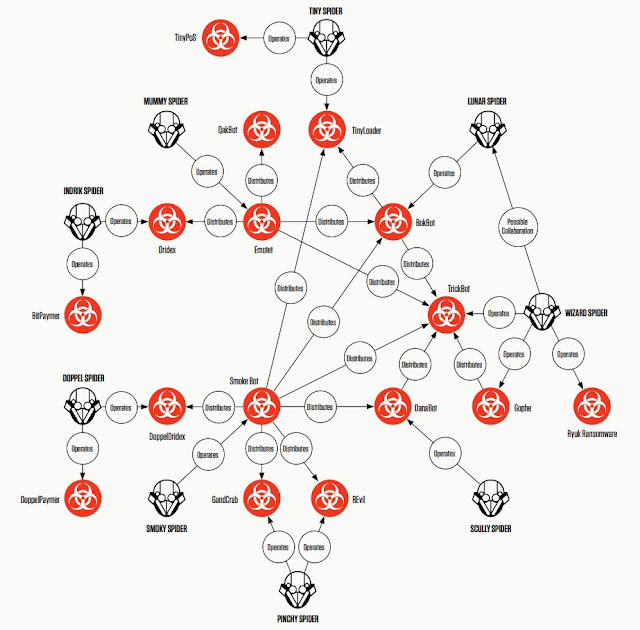 CrowdStrike Actor Labels for Emotet => Trickbot => Ryuk etc.In the Crowdstrike worldview, "Mummy Spider" is the actor(s) behind Emotet, who serves his customer "Wizard Spider" by delivering Trickbot for him/them. Post infection with Trickbot, Wizard Spider may choose to infect with Ryuk Ransomware. Per Crowstrike, Lunar Spider (the operator of BokBot AKA IcedID) and Scully Spider (the operator of DanaBot) also occasionally are used to distribute Trickbot. But mostly, its Emotet.
CrowdStrike Actor Labels for Emotet => Trickbot => Ryuk etc.In the Crowdstrike worldview, "Mummy Spider" is the actor(s) behind Emotet, who serves his customer "Wizard Spider" by delivering Trickbot for him/them. Post infection with Trickbot, Wizard Spider may choose to infect with Ryuk Ransomware. Per Crowstrike, Lunar Spider (the operator of BokBot AKA IcedID) and Scully Spider (the operator of DanaBot) also occasionally are used to distribute Trickbot. But mostly, its Emotet.
 DINJ file breakdown (04MAR2020 by @GarWarner)
DINJ file breakdown (04MAR2020 by @GarWarner)The DINJ file for trickbot contain lists of URL patterns labeled with markup tags / .
In the file I used for this analysis, updated from the Command & Control on 04MAR2020, there were 84 "igroups" containing 329 URL patterns, targeting 131 named domains. In the current DINJ file, the most common target is Japanese banks and financial institutions. Each of the 41 URLs below were for Japanese organizations: 82bank.co.jpeposcard.co.jplifecard.co.jpshinkin-ib.jp.aeon.co.jpfukuokabank.co.jpmichinokubank.co.jpshinwabank.co.jpaeonbank.co.jpgogin.co.jpmiyagin.co.jpshizugin.netamazon.co.jpgunmabank.co.jpmizuhobank.co.jpshizuokabank.co.jpanser.ne.jphigobank.co.jpmufg.jpshokochukin.co.jpawabank.co.jphirogin.co.jpncbank.co.jptominbank.co.jpbk.mufg.jphokkokubank.co.jporico.co.jptsukubabank.co.jpchibabank.co.jphokuyobank.co.jppocketcard.co.jpvpass.ne.jpchugin.co.jpjaccs.co.jprakuten.co.jpyamagatabank.co.jpchushin.co.jpjuroku.co.jpryugin.co.jpdaishi-bank.co.jpkeiyobank.co.jpsaisoncard.co.jp US Banks were second in popularity 53.comcitizensbankonline.comiccu.comregions.comally.comcu1.orgiconnectdata.comsecureinternetbank.comamegybank.comdiscover.comkey.comsuntrust.comamericanexpress.comebanking-services.commtb.comusaa.combankofamerica.comefirstbank.comnavyfederal.orgusbank.combmo.comfirelandsfcu.orgnbarizona.comvancity.comcapitalone.comhuntington.comonlinebank.comvectrabank.comccservicing.comibanking-services.compaypal.comzionsbank.comchase.compnc.com Followed by German Banks bawagpsk.comconsorsbank.deing-diba.deraiffeisen.atberliner-bank.dedeutsche-bank.delzo.comsantander.decomdirect.dehaspa.denorisbank.desparda.decommerzbank.deing.depostbank.detargobank.de Some of the other targets were especially interesting to me. The Brokerages: Ameritrade.com, eTrade.com, Schwab.com The Big Retails: Amazon.com, BestBuy.com, CostCo.com, eBay.com, Grainger.com, SamsClub.com The CryptoCurrency Exchanges/Companies: Binance.com, BitFinex.com, BitStamp.com, Blockchain.com, CoinBase.com, CoinMarketCap.com, CryptoCompare.com, DogeChain.info, Kraken.com, Paxful.com And two Payroll companies, which may be especially interesting as we are in Tax Season in the USA. Curiously these two are both part of the same "igroup": ADP.com and Paychex.com Especially since they are targeting ADMINISTRATORS of those Payroll systems, based on the strings I'm seeing: *runpayroll.adp.com/* myapps.paychex.com/*_remote/* If you are curious to see more of the current DINJ file, I've shared it as a PasteBin file here: GarWarner's Trickbot DINJ file 04MAR2020 (updated URL: Pastebin removed the first one, trying again.) URL Patterns in Trickbot DINJ
Some patterns do not identify a domain, such as the pattern "https://.*.de/privatkunden/*" (which says "we don't care which German Bank we're looking for, but if they have a URL that includes "private customers", go ahead and grab stuff from there. The pie chart above only maps organizations where a full domain was identified. Remember that the default is GRAB EVERYTHING, but URLs with specific strings on a site will be sent back to the criminals "tagged for action" making it easier for them to harvest and take action on those pages. Here's an example of URLs related to NavyFederal: So, while there may be many other places on the NavyFederal website that request user interaction, three particular URL patters are targeted for prioritized collection. The "s=" number tells which iGroup the URL belongs to (all of the URLs in 1535723065134935 belong to Navy Federal), the "id=" tells what sub-URL the visitor was on when they submitted this particular data. The "Ignore-Mask" flag can be used to tell Trickbot not to gather particular data (for example, in the NavyFederal block above, it says Ignore everything related to Javascript and Stylesheet pages), or to say "Don't gather this data as part of the current "LM" because we already got it elsewhere, as seen in this Norris Bank block: In this iGroup for NorisBank, there are three specific patterns that each extract data to a particular location, so when the generic pattern "*norisbank.de*" is used, it instructs the bot not to include those subURLs that have already been captured separately.A Bit of Spam Context
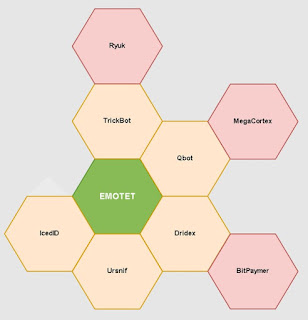
As everyone probably knows by now, the top spamming botnet since the death of Kelihos has been Emotet. Emotet is involved in the distribution of several banking trojans, including TrickBot which is known to be the main source of Ryuk ransomware infections, and Qbot, which often leads to MegaCortex ransomware, and even Dridex, which sometimes leads to BitPaymer ransomware. There are many great Emotet/Trickbot researchers out there, especially the @Cryptolaemus research group, which shares Emotet Indicators of Compromise regularly, and @pollo290987, who shared this graphic on his Twitter feed: Trickbot is ALSO distributed by other sources, which Crowdstrike does a great job of illustrating in this diagram that maps out the relationships between spambots and malware payloads: CrowdStrike Actor Labels for Emotet => Trickbot => Ryuk etc.In the Crowdstrike worldview, "Mummy Spider" is the actor(s) behind Emotet, who serves his customer "Wizard Spider" by delivering Trickbot for him/them. Post infection with Trickbot, Wizard Spider may choose to infect with Ryuk Ransomware. Per Crowstrike, Lunar Spider (the operator of BokBot AKA IcedID) and Scully Spider (the operator of DanaBot) also occasionally are used to distribute Trickbot. But mostly, its Emotet.
CrowdStrike Actor Labels for Emotet => Trickbot => Ryuk etc.In the Crowdstrike worldview, "Mummy Spider" is the actor(s) behind Emotet, who serves his customer "Wizard Spider" by delivering Trickbot for him/them. Post infection with Trickbot, Wizard Spider may choose to infect with Ryuk Ransomware. Per Crowstrike, Lunar Spider (the operator of BokBot AKA IcedID) and Scully Spider (the operator of DanaBot) also occasionally are used to distribute Trickbot. But mostly, its Emotet.