Once I change my Chrome Virtual Machine to pretend to be "Safari on iPhone" we revisit the URL that was sent to my phone:
We've written several times in the past about these never-ending surveys. Their objective is to gather as much personal data from you as they can and to show you as many advertisements as they can. They then experience revenue by both showing you ads during the survey, but also by selling the personal information that they gather you to organizations that need "qualified sales leads." They will tell those organizations that you are looking for things like savings on college tuition, health insurance, car insurance, electronics, a new vehicle, etc, and you will start getting more spam messages from those organizations who will have believed that you asked for their spam!
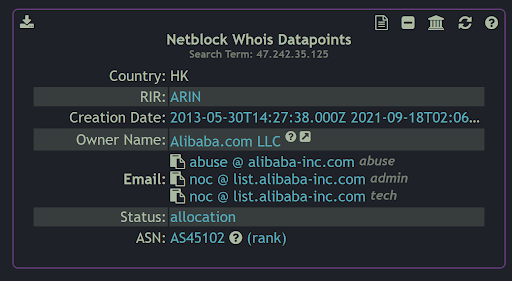
We asked our friends at Zetalytics, via their Zone Cruncher tool, "So where in the world is the IP address n9cxr[.]info?" They told us that it is located in Hong Kong on a server that is hosted by Alibaba Inc.
That's very interesting! Thanks, Zetalytics! Could you also tell us OTHER DOMAIN NAMES that have recently been seen on that same IP address? After all, we've received three such domains in the three messages that I received on my personal phone!
All of those domains are of course registered at the scummy domain registrar NameCheap. They claim that if we inform them of bad domains, they will de-register them. Once I post this, I'll send them a copy and report back what happens.
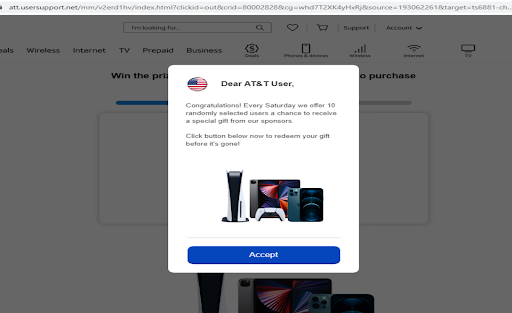
By the way, the content is not exactly the same with each visit. My next visit to the n9cxr URL gave me this pop-up instead:
So how are we getting to the fake AT&T page? That's where a tool that CAUCE Director Neil Schwartman showed me comes in. While I don't recommend the company necessarily, this little Chrome plug-in is gold for mapping out redirect paths! (Search for the Chrome Extension "Ayima Redirect Path" and please remember you should only be reviewing potentially hostile URLs in a Virtual Machine!)
What does all that mean? It tells us that the first URL's webserver claimed that the page we were looking for "dhmxmcmBTQ" had been temporarily redirected to "themechallenge[.]club" and that we should ask that server for a particular "key."
That key caused the server to send us a Javascript that redirected us to another URL on their website, which in turn did a "META Redirect" to the webserver "go.metreysi[.]info" where we should tell them we were sent by a certain "cnv_id." That server then pretended that we had clicked on it, and sent us via another "302 temporary redirect" to a webserver called "redirect.usersupport[.]net." UserSupport then did yet another redirect which took us to the webside "att.usersupport[.]net."
More domains to look up in ZoneCruncher!
https://themechallenge[.]club/click.php?key=abrrkduwznt79g18cx66
go.metreysi[.]info => hosted on LeaseWeb at 23.108.57[.]187 redirect.usersupport[.]net => hosted on 2606:4700:3032::6815:2b25
att.usersupport[.]net => hosted on 2606:4700:3031::ac43:da02
I'm guessing that all of these other "go" sites that are sharing the same IP address will also be involved in illegal "redirection" scams that start off with SMS Blasting.
By the way, do you remember the "key" we had to pass? In a similar way to our User-Agent, if you visit one of these sites and fail to pass it a "key" it will just redirect you to 127.0.0.1, which means, "visit your own machine."
Not just AT&T!
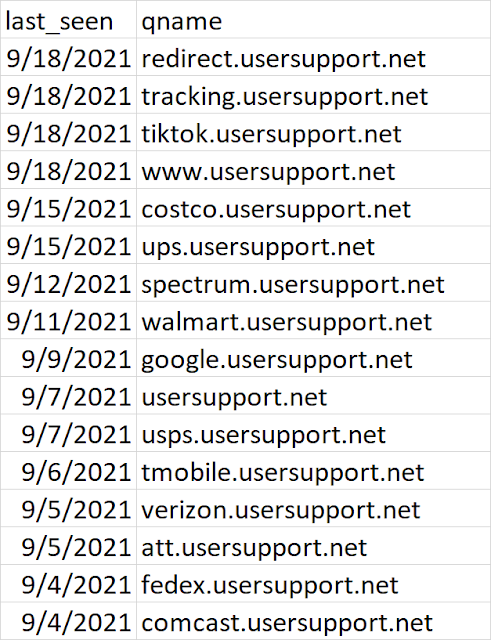
One of Zetalytics other tricks is being able to show me other hostnames on the same domain. (The term for this is called "PassiveDNS")
It looks like "UserSupport[.]net" is also being used to imitate TikTok, CostCo, Walmart, and Google, shipping company UPS, FedEx, and US Postal Service, and Cell phone providers, AT&T, Comcast, Spectrum, T-Mobile, and Verizon!
Because I haven't received those particular SMS messages, I can't navigate to them. (I have the wrong "key" to get the chain started.) But I'd love to see some more of these if you would be willing to share a screenshot! List of SMS-spam-abusing .info (and .xyz) domains believed to be associated with these campaigns. It sort of makes sense that there are exactly 100 of them.
1find[.]info
1fwnx[.]info
1nvc[.]info
2edcc[.]info
2gtex[.]info
2ofgm[.]info
3mgie[.]info
3ohmd[.]info
4gogm[.]info
4onnr[.]info
4onnr[.]info
6ghme[.]info
6nbfu[.]info
6omrf[.]info
6wqbv[.]info
7botm[.]info
7gboe[.]info
7gboe[.]info
7uwhn[.]info
7wxcd[.]info
8bmxw[.]info
9bmdx[.]info
a2sct[.]info
a7tev[.]info
appsc[.]info
appsf[.]info
bjdz2[.]xyz
bmeq9[.]info
bookc[.]info
bookx[.]info
cartm[.]info
cartm[.]info
cartz[.]info
faceg[.]info
faceg[.]info
faceh[.]info
facem[.]info
faceu[.]info
facey[.]info
fuwd2[.]info
gg0l[.]info
gi3t[.]info
gi3t[.]info
gitn4[.]info
goen4[.]info
gotr6[.]info
gr8f[.]info
havec[.]info
havec[.]info
havec[.]info
havec[.]info
havec[.]info
havec[.]info
havej[.]info
havew[.]info
hidej[.]info
hidej[.]info
hidem[.]info
hidep[.]info
hidep[.]info
j1bcs[.]info
j1bcs[.]info
j2bmf[.]info
k2ave[.]info
k4acr[.]info
k4acr[.]info
k8bvz[.]info
kpl5[.]info
kpp8[.]info
kpp8[.]info
kse0[.]info
ktf4[.]info
l1bmz[.]info
l5brv[.]info
lgte3[.]info
m2cxn[.]info
m6cda[.]info
mbdz2[.]xyz
mqbvn[.]info
n4csv[.]info
n9cxr[.]info
nameb[.]info
pexw0[.]xyz
qkkk2[.]xyz
raini[.]info
rainl[.]info
rainz[.]info
s1vrk[.]info
s2avr[.]info
s2avr[.]info
s4asc[.]info
s6axe[.]info
s7axm[.]info
s8avx[.]info
toer9[.]info
toer9[.]info
vbjh9[.]xyz
wodm7[.]info
wordc[.]info
wosn9[.]info